Vulnerability Management Courses
Vulnerability Management Courses - Vulnerability management foundation (optional) understand the basics of vulnerability management. The vulnerability management lifecycle across various platforms: Web vulnerability management learning path: These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Describe the effectiveness of vm solution in terms of network monitoring, identifying risks. The course also includes lab simulation of vulnerability management processes. Cwe, patch management, ransomware, zones of vulnerabilty. Steps to create, mature, and implement a vulnerability management program. Remember, vulnerability management is a continuous journey — one that evolves with the changing technology landscape. In this course, you will get an insight into the core functions of qualys vmdr. Learn more about the features here. Web explain the need for vulnerability management. In this course, you will get an insight into the core functions of qualys vmdr. Vulnerability management, detection, and response an introduction to core qualys sensors and core vmdr functionality. Web as you progress through the vulnerability management courses, you learn how to set up a virtual. Web introduction to vulnerability management get started now ine business plans what about this course? These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Identify different options for vulnerability management. Web our vulnerability management online training courses from linkedin learning (formerly lynda.com) provide you with the skills you need,. Less time and effort to assess, prioritize and remediate issues. Courses with certifications provide videos, labs, and exams built to help you retain information. These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. The course also includes lab simulation of vulnerability management processes. The vulnerability management lifecycle across various. These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Web learning paths and training courses. Less time and effort to assess, prioritize and remediate issues. Web cybersecurity management the master of science in cybersecurity management program, offered by the college of business and management, is designed to empower graduate. Web as you progress through the vulnerability management courses, you learn how to set up a virtual testing environment and identify, prioritize and remediate vulnerabilities. Describe the effectiveness of vm solution in terms of network monitoring, identifying risks. Web what you'll learn understand what vulnerabilities are and how they are important in the field of cyber security. Web vulnerability management. Cwe, patch management, ransomware, zones of vulnerabilty. Set the scope of vulnerability management. Web vulnerability management with online courses and programs. By staying vigilant and adopting these best practices, you can safeguard your software and data. Certifications are the recommended method for learning qualys technology. Web explain the need for vulnerability management. Web there are 4 modules in this course. The course dives into detail information of on the critical issues of vulnerabilities. Web learning paths and training courses. Web what you will learn the foundational concepts and importance of vulnerability management. This course builds on the material in the nessus fundamentals course. Web stay ahead in the battle against ransomware by staying informed and prepared. From asset discovery to vulnerability assessment to compliance, participants will learn to effectively utilize nessus in a variety of business use. Specific course topics include pattern discovery, clustering, text retrieval, text mining and analytics, and data. Web cybersecurity management the master of science in cybersecurity management program, offered by the college of business and management, is designed to empower graduate students with essential leadership, analytical, and management skills vital for cybersecurity management roles in various sectors, including private, public, and. Web what you'll learn understand what vulnerabilities are and how they are important in the field. Web learning paths and training courses. Cisa has added one new vulnerability to its known exploited vulnerabilities catalog, based on evidence of active exploitation. Describe the effectiveness of vm solution in terms of network monitoring, identifying risks. Web illinois offers a variety of courses, including courses for the online master's program, and many research opportunities in information security and cyber. Web this vulnerability management training course will show you the most effective ways to mature your vulnerability management program and move from identifying vulnerabilities to successfully treating them. The vulnerability management lifecycle across various platforms: Web what you will learn the foundational concepts and importance of vulnerability management. This course builds on the material in the nessus fundamentals course. Get more insights on 3 actions to prevent ransomware and watch for more insights, strategies, and updates on effectively combating ransomware threats. Courses with certifications provide videos, labs, and exams built to help you retain information. Identify and manage vulnerabilities which pose a cyber security threat. It covers risk management and covers the basis of penetration testing vs vulnerability management as well. Web cybersecurity management the master of science in cybersecurity management program, offered by the college of business and management, is designed to empower graduate students with essential leadership, analytical, and management skills vital for cybersecurity management roles in various sectors, including private, public, and. Web there are 4 modules in this course. These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. The course also includes lab simulation of vulnerability management processes. Cwe, patch management, ransomware, zones of vulnerabilty. Steps to create, mature, and implement a vulnerability management program. Web our vulnerability management online training courses from linkedin learning (formerly lynda.com) provide you with the skills you need, from the fundamentals to advanced tips. Web illinois offers a variety of courses, including courses for the online master's program, and many research opportunities in information security and cyber defense to both undergraduate and graduate students.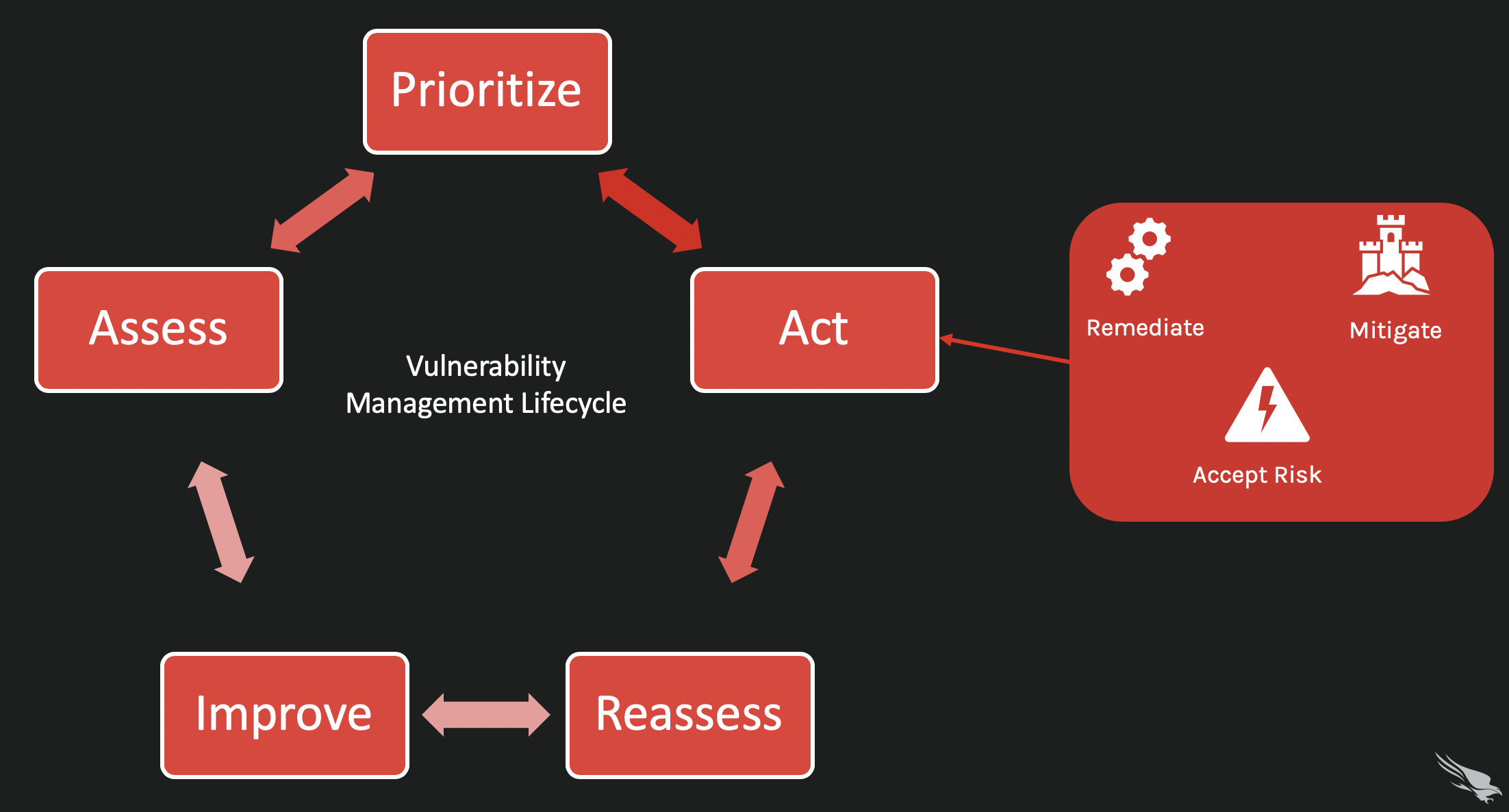
The Vulnerability Management Lifecycle (5 Steps) CrowdStrike

Vulnerability Management Lifecycle, Tools, and Best Practices
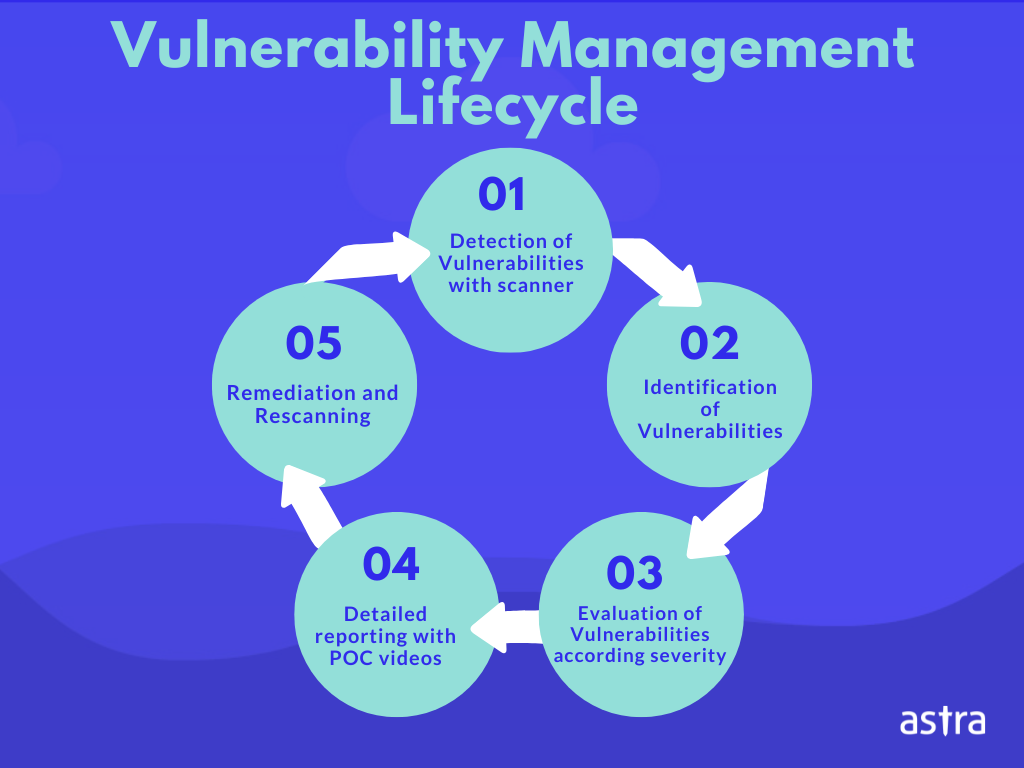
What is Vulnerability Management? Astra Security Blog
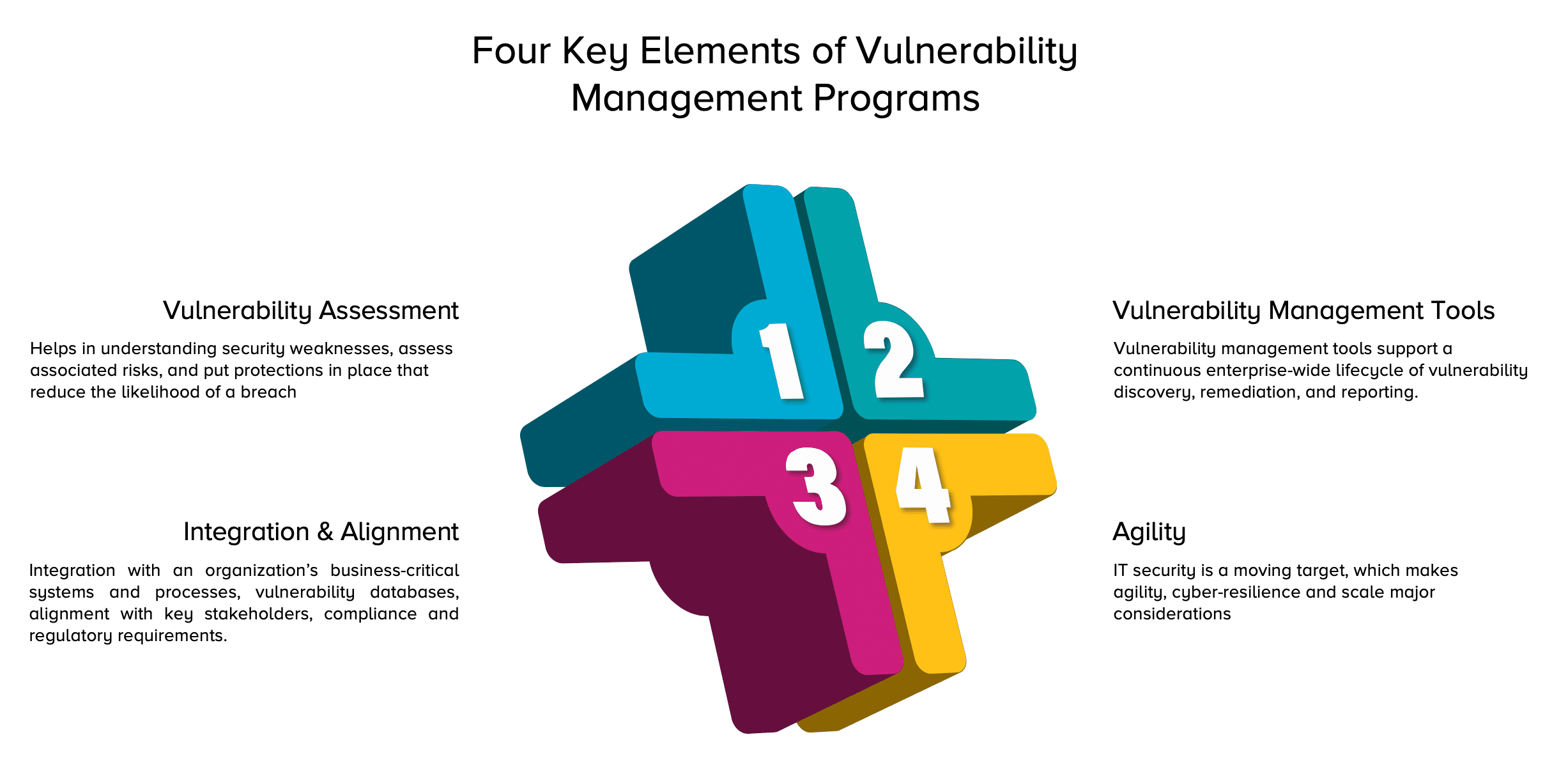
Vulnerability Management Program How to Built It? Balbix

Introduction to Vulnerability Management BMC Software Blogs
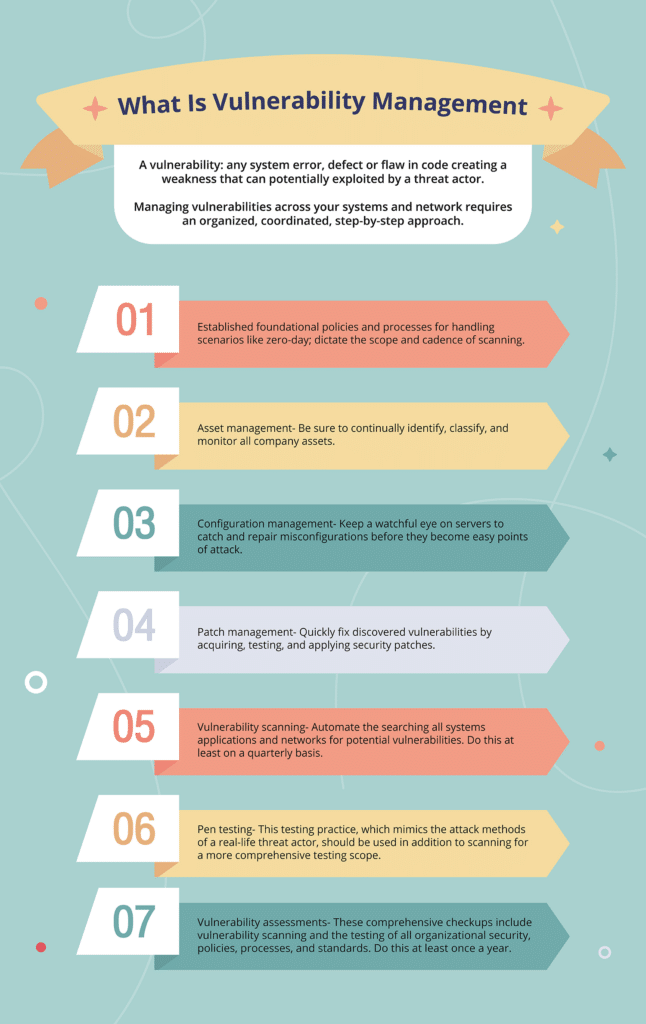
The Ultimate Guide to Vulnerability Management Hyperproof

Creating a Vulnerability Management Strategy zSecurity

Vulnerability Management System The Definitive Guide (2022) Cyvatar

Vulnerability Management Lifecycle Best Guide in 2023

The Five Stages of Vulnerability Management
Web As You Progress Through The Vulnerability Management Courses, You Learn How To Set Up A Virtual Testing Environment And Identify, Prioritize And Remediate Vulnerabilities.
Web The Data Mining Specialization Teaches Data Mining Techniques For Both Structured Data Which Conform To A Clearly Defined Schema, And Unstructured Data Which Exist In The Form Of Natural Language Text.
List The Best Practices Of Vulnerability Management.
Web 11 Ceu/Cpe Course Content Introduction Vulnerability Assessment Tools 8M Vulnerability Management Lifecycle 7M Introduction To Vulnerabilities 10M Course Introduction 4M Vulnerability Assessment Labs Core Impact Vulnerability Scan 0M Creating Recommendations Based On Vulnerability Assessments 0M Manual Vulnerability.
Related Post: